Table of Contents
What is SSL?
Secure Sockets Layer (SSL) is a standard security protocol for establishing encrypted links between a web server and a browser in online communication. The SSL protocol ensures that all data transmitted between the web server and browser remains encrypted, thus safeguarding it from being intercepted by unauthorized entities. SSL protects sensitive data transmissions such as login credentials, credit card numbers, or personal information that is exchanged during online transactions or access to web services.
As a part of the web application’s architecture, SSL operates at the transport layer of the network protocol stack, acting as a security-enhanced version of the transport layer protocols like TCP (Transmission Control Protocol). When a client browser wants to connect securely to a web application, it starts an SSL ‘handshake’ process. This process involves the exchange of cryptographic keys between the client and server, leading to the creation of a secure, encrypted communication channel.
SSL is an important part of web application architecture for securing online communications. If you want to know about web application architecture in-depth, refer to the blog on web application architecture. It’s a comprehensive guide that helps you understand how to create and manage safe and efficient web applications.
How Does Secure Sockets Layer Work?
Secure Socket Layer (SSL) often works in conjunction with a reverse proxy server for added security and efficiency. Here is a simplified step-by-step breakdown of how SSL works:
- Client Hello: The client, typically a web browser, initiates the SSL/TLS process by sending a “Client Hello” message to the server. This message outlines the client’s SSL/TLS capabilities, including the versions and cipher suites it supports.
- Server Hello: The server, often acting as a reverse proxy to handle client requests and server responses, responds with a “Server Hello” message. The server selects the highest level of SSL/TLS protocol and the most secure cipher suite that both the client and server support. At this stage, the server sends its SSL/TLS certificates to the client for authentication purposes, and if a client-side certificate is required, this request is also made.
- Certificate Verification: The client verifies the server’s SSL certificate with a trusted Certificate Authority (CA). This can happen even if a reverse proxy is used, as the proxy can pass the SSL certificates to the client for verification.
- Secret Generation: The client creates a pre-master secret for SSL communication and encrypts it using the server’s public key. This encrypted pre-master secret is then sent to the server, which uses its private key to decrypt it. From this pre-master secret, both the client and server independently generate the same “master secret”.
- Key Generation and Exchange: Using the master secret, session keys are generated. A “finished” message is exchanged, encrypted with the secure session key, indicating a successful handshake.
- Secure Communication: The client and server now exchange information securely, encrypted with the session key.
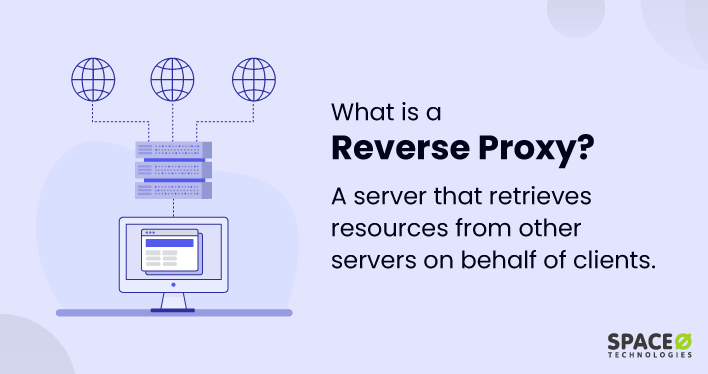
The above steps show the step-by-step working of SSL. By using a reverse proxy, you can offload some of the computational efforts associated with SSL/TLS, enhancing the overall performance of secure internet communication. Want to know more about a reverse proxy? Know about its concept from the post of what is a reverse proxy. From this post, you will have an in-depth understanding of the definition and its importance.
What are the Benefits of Secure Sockets Layer?
Secure Sockets Layer (SSL) plays a vital role in internet security. Here are the 5 core benefits of a secure sockets layer:
- Data Protection: SSL protects data during transmission by providing end-to-end SSL encryption of the data transferred between the client and server. This means that sensitive information such as credit card numbers, social security numbers, and login credentials are all kept secure from potential cyberattacks or eavesdropping.
- Identity Verification: SSL includes a process of authentication that verifies the identity of the parties involved in the communication. SSL certificates are issued by Certificate Authorities (CAs) who validate the identity of the website and its owner before issuing the certificate. This helps prevent phishing attacks, where malicious websites impersonate legitimate ones to trick users into providing personal information.
- Trust and Credibility: Websites with an SSL certificate display a padlock in the address bar, and the HTTP is replaced with HTTPS (where “S” stands for secure). This visual cue assures visitors that their connection is secure, fostering trust. This can be especially crucial for e-commerce and banking websites where financial transactions take place.
- SEO Ranking: Search engines like Google consider website security as a ranking factor. Websites with SSL certificates are more likely to rank higher in search engine results pages (SERPs) than those without.
- Regulatory Compliance: In certain industries, the use of SSL is a requirement for regulatory compliance. For example, standards like the Payment Card Industry Data Security Standard (PCI DSS) require a secure connection for all credit card transactions.
By providing encryption, authentication, and integrity, SSL is fundamental in building a secure internet.
In conclusion, Secure Sockets Layer (SSL) and its successor, Transport Layer Security (TLS), are vital for maintaining a secure and trustworthy internet. They utilize public and private keys, encryption algorithms, and TLS certificates issued by a certification authority to ensure that all data exchanged between the client and server remains encrypted. In essence, SSL and TLS are the cornerstones of web security, safeguarding our online interactions by ensuring the confidentiality, integrity, and authenticity of the encrypted data we exchange daily.