Table of Contents
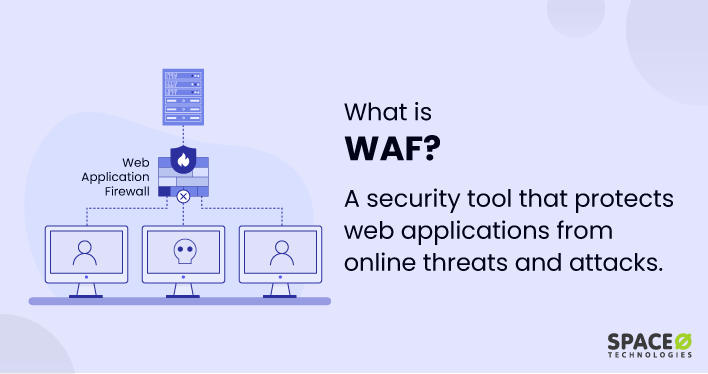
What is WAF? (Web Application Firewall)
A web application firewall (WAF) is a security tool that protects web applications from various cyber threats and attacks. It acts as a barrier between web servers and users by analyzing and filtering HTTP/HTTPS traffic, monitoring requests, and blocking malicious activities.
A WAF operates at the application layer of the network stack and inspects incoming requests and outgoing responses. It helps identify and block common web application vulnerabilities, such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
To maximize the effectiveness of a WAF, it should be deployed together with other best practices for web application security. If you want to know, the best security practices for web applications read our blog on best web application security practices. Reading this blog will help you to use security practices while implementing web application firewalls.
If you’re not fully familiar with the concept of security in web apps, you can go through this post which defines web application security. This resource will help in understanding its importance and its implementation in web apps.
How Does Web Application Firewall Work?
Here is a complete working process of the web application firewall.
- The WAF intercepts incoming HTTP/HTTPS requests and outgoing responses between a user and a web application, acting as a robust server plugin. As a proxy, it implements a negative security model, blocking known threats and allowing other traffic. This negative security model is based on a comprehensive list of attack signatures and traffic patterns known to be harmful.
- The WAF applies a set of predefined rules and a security policy to the web traffic. These rules are based on known attack patterns, vulnerabilities, and application-specific security requirements. If a request matches a rule associated with a known attack, the WAF takes action to block or mitigate the threat.
- The WAF utilizes a database of known attack signatures and patterns to detect and block malicious traffic. These signatures represent specific patterns or payloads commonly associated with attacks like SQL injection or XSS. If a request contains a matching signature, the WAF takes appropriate action.
- Some advanced WAFs incorporate behavioral analysis techniques to identify abnormal patterns and deviations from normal application behavior. By analyzing request attributes, session data, and user behavior, the WAF can detect potential application layer attacks or suspicious activities that may not have a known signature.
- WAFs use anomaly detection algorithms to identify unusual or unexpected behavior in web traffic. This method compares the current traffic patterns against a baseline of normal behavior and raises alerts or takes action when significant deviations are detected.
- When a threat is identified, the WAF takes appropriate action and protects web apps. This includes blocking the request, redirecting it to a different page, or dynamically modifying the request to remove or neutralize the threat. The WAF also logs the incident for further analysis and reporting.
- Web application firewalls, whether host-based WAF or network-based hardware appliances, often provide logging and reporting capabilities, allowing administrators to review and analyze traffic patterns, detected threats, and system performance. These logs can help in identifying attack trends, fine-tuning security policies, and responding to security incidents.
7 Benefits of Web Application Firewall
Web Application Firewalls (WAFs) offer several benefits in terms of web application security. Here are some key advantages:
Provides Protection Against Common Attacks
WAFs provide defense against a wide range of common web application attacks, such as SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and more. While traditional firewalls provide a basic level of defense, a next-generation firewall, with integrated WAFs, elevates the protection by blocking malicious traffic and filtering out suspicious requests, significantly reducing the risk of successful attacks.
Improves Application Security
WAFs, operating as a proxy, help enhance the overall security posture of web apps. By implementing security policies, enforcing best practices, and mitigating known vulnerabilities, they reduce the likelihood of breaches, unauthorized access, and sensitive data leaks.
Offers Real-time Threat Detection
WAFs employ advanced detection techniques, including signature-based filtering, behavioral analysis, and anomaly detection, to identify and respond to threats in real-time. This proactive approach enables rapid identification and mitigation of potential attacks, minimizing the impact on web apps.
Facilitates Customizable Security Policies
WAFs allow administrators to configure and customize security policies according to the specific needs of their web applications. This flexibility ensures that the WAF can adapt to different application requirements while providing robust protection against evolving threats.
Provides DDoS Mitigation Capabilities
Many WAF solutions include Distributed Denial of Service (DDoS) protection capabilities. By detecting and mitigating DDoS attacks, they help ensure the availability and continuous operation of web applications, even during high-traffic or malicious onslaughts.
Compliance and Regulatory Requirements
WAFs assist organizations in meeting compliance standards and regulatory requirements, such as the Payment Card Industry Data Security Standard (PCI DSS) or the General Data Protection Regulation (GDPR). By implementing a WAF, businesses can fulfill security obligations and maintain the confidentiality and integrity of customer unauthorized data.
Logging and Reporting
WAFs often provide detailed logs and comprehensive reporting capabilities, allowing administrators to monitor and analyze web traffic, detected threats, and system performance. These logs can aid incident response, forensic analysis, and ongoing security audits.
Overall, deploying a web application firewall offers robust protection, enhances application security, and helps organizations maintain a strong defense against web-based attacks.
A Web Application Firewall (WAF) is a vital security measure for protecting web applications from a wide array of cyber threats. Utilizing a positive security model, the WAF only permits known, trusted traffic, effectively blocking all unrecognized, potentially malicious activities. By analyzing, filtering, and blocking malicious traffic in real time, a WAF enhances overall security, supports compliance with regulatory standards, and facilitates incident response and threat analysis. As cyber threats continue to evolve, WAFs provide a dynamic and adaptable line of defense, ensuring the integrity and continuity of web services.